Similar as other Trojan malware, Exploit.CVE-2014-1761.Gen is programmed to make some benefit for those virus producers and could be spread via the internet in quick speed. Every time when you boot up the machine, Exploit.CVE-2014-1761.Gen will come back and notify you of continuous pop-ups and security alerts. Due to the presence of the malware, you may be unable to execute any system application, and worse you may be blocked from editing registry editor or task manager. Besides, other weird symptoms happen, such as the speed of PC system decreases, internet speed disconnects from time to time, unknown programs appear on your desktop, and so on. Another worse thing is that remote hackers could be allowed to access your machine and steal your confidential information like log-in details for illegal benefits. You shall take right action to remove Exploit.CVE-2014-1761.Gen quickly from your PC once detection. Here is our manual and automatic Exploit.CVE-2014-1761.Gen removal guide for your reference.
Common Symptoms Caused by Exploit.CVE-2014-1761.Gen
1.It invades system without any permission2.It has bad reputation & impact online
3.It spreads to removable drives and other PCs quickly
4.It may bring along all kinds of spyware program
2 Solutions for Exploit.CVE-2014-1761.Gen Removal
Solution 1: Manual Removal
Solution 2: Automatic Removal
Solution 1: Manual Removal
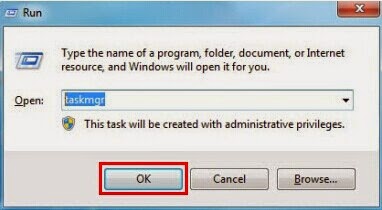
Step one: End processes that Exploit.CVE-2014-1761.Gen has run on your system.
(Guides: Press CTRL+ALT+DEL or CTRL+SHIFT+ESC or Press the Start button->click on the Run option->Type in taskmgr and press OK.)
Step two: Delete files that Exploit.CVE-2014-1761.Gen has added to your system folders and files.
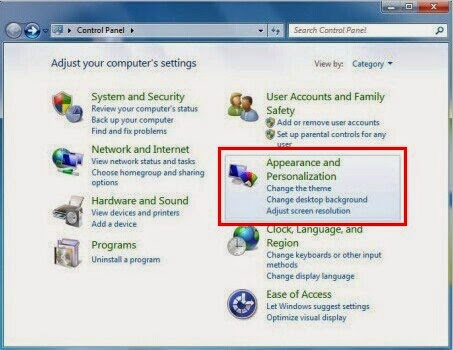
Show all hidden files
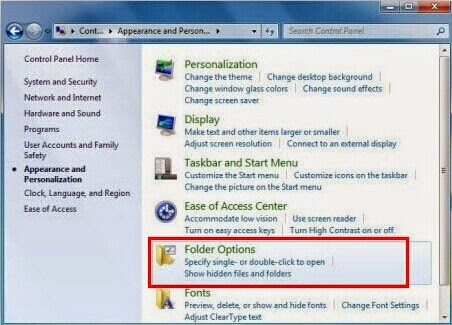
a) Click the Start menu and choose Control Panel, select Appearance and Personalization, to find Folder Options then double-click on it.
b) In the pop-up dialog box, click the View tab and check Show hidden files and folders.
Delete all the malicious files about this infection as below.
C:\windows\system32\drivers\mrxsmb.sys(random)
C:\WINDOWS\system32\drivers\redbook.sys(random)
%AllUsersProfile%\Application Data\.exe
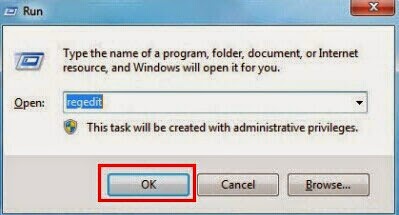
Step three: Remove registries that Exploit.CVE-2014-1761.Gen has created to your system registry editor.
(Steps: Hit Win+R keys and then type regedit in Run box to search)
Get rid of all the related registry entries listed below
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system “ConsentPromptBehaviorUser” = 0 HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System“DisableRegedit” = 0HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
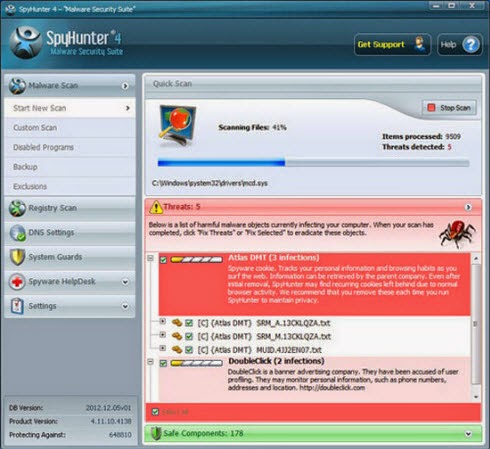
Solution 2: Automatic Removal
1) Click the icon below to download SpyHunter removal tool.
2) Follow the instructions to install SpyHunter.
3) Run SpyHunter and start a full scan to detect any PC invader.
4) Show results after the scan finishing and remove all detected harmful components.
Please be careful that not all victim users can manually remove Exploit.CVE-2014-1761.Gen with success, since some infectious files might be hidden or altered to avoid from being deleted completely. You should realize the manual removal is a tough process requiring sufficient computer troubleshooting skills. To save your time and hassle, it’s recommended that you download this powerful Malware Removal Application to get rid of the virus thoroughly.






No comments:
Post a Comment