Iminent Toolbar is an annoying program that offers a web search engine named search.iminent.com, which is being promoted via some free applications downloaded onto the affected computer. The appearance of search.iminent.com looks like a legit website which contains a typical search bar and search menu. However, it in fact belongs to a web browser hijacker virus, installing onto your PC together with other malware or spyware. It’s designed by cyber criminals to lock your homepage as its domain and replace your default search engine. This activity is always performed furtively without any permission asked. Undoubtedly, there are many harmful advertisements and sponsored links embedded in its related search results, which is utilized by schemers to generate illegal revenue. Besides, due to this redirect malware, the performance of the PC will be strikingly degenerated, with occasional system freezes or crashes from time to time. Taking a series of hazards triggered by iminent, it’s strongly recommended to uninstall it as soon as possible.
Learn to remove Spyware/Virus easily and completely.
Wednesday, June 26, 2013
Remove The Department of Justice Virus (U.S. Department of Justice Ransomware Removal)
 Department of Justice Virus, also known as The United States Department of Justice virus, U.S. Department of Justice virus, and DOJ virus (D.O.J. virus), is another variant of notorious Moneypak virus categorized as ransomware. Being infected with this virus, your PC will be suspended on the grounds of violation of the law of the United States of America, while the truth is that it’s simply a false warning alert forging the badge of the real United States Department of Justice, in the purpose of intimidating unwary users who encountered with this ransomware to pay a ransom of usually $300 via payment card such as Moneypak or Paysafecard, etc., within the allotted time of 48 hours. Pay attention here, the Department of Justice virus is a total scam whose makers aim to swindle victims out of money. By seeking for system vulnerabilities or spreading via spam mails or fake torrent files, this ransomware gets installed your machine without any awareness. Once downloaded, it would completely lock your PC and leave its scary message, informing you that you’ve been broken the Copyright and Related Rights Law and illegally using or distributing copyrighted content. It also shows the infected PC’s IP address, host name and even turns on your webcam without any permission asked. In order to deblock your machine, it’s demanded to pay for a certain sum of money as ransom. Many people would recklessly do what the virus instructs them to do; however, after the payment, the virus is still there and even asks for more fines. It is noticeable that Department of Justice virus is nothing but a hoax designed to frighten you and rip you off.
Department of Justice Virus, also known as The United States Department of Justice virus, U.S. Department of Justice virus, and DOJ virus (D.O.J. virus), is another variant of notorious Moneypak virus categorized as ransomware. Being infected with this virus, your PC will be suspended on the grounds of violation of the law of the United States of America, while the truth is that it’s simply a false warning alert forging the badge of the real United States Department of Justice, in the purpose of intimidating unwary users who encountered with this ransomware to pay a ransom of usually $300 via payment card such as Moneypak or Paysafecard, etc., within the allotted time of 48 hours. Pay attention here, the Department of Justice virus is a total scam whose makers aim to swindle victims out of money. By seeking for system vulnerabilities or spreading via spam mails or fake torrent files, this ransomware gets installed your machine without any awareness. Once downloaded, it would completely lock your PC and leave its scary message, informing you that you’ve been broken the Copyright and Related Rights Law and illegally using or distributing copyrighted content. It also shows the infected PC’s IP address, host name and even turns on your webcam without any permission asked. In order to deblock your machine, it’s demanded to pay for a certain sum of money as ransom. Many people would recklessly do what the virus instructs them to do; however, after the payment, the virus is still there and even asks for more fines. It is noticeable that Department of Justice virus is nothing but a hoax designed to frighten you and rip you off.Department of Justice Virus is such a harmful item
* It can compromise your system and may introduce additional infections like rogue software.* It enters your computer without your consent and disguises itself in root of the system.
* This virus often takes up high resources and strikingly slow down your computer speed.
* It can help the cyber criminals to track your computer and steal your personal information.
* It may force you to visit some unsafe websites and advertisements which are not trusted.
How to unlock your computer from Department of Justice Virus?
Reboot the PC and keep pressing F8 key on the keyboard upon PC startup but before logging in. Hit the arrow keys to choose "Safe Mode with Networking" option, and then tap Enter key to enter Safe Mode with Networking.Kill malicious processes:
Delete infected files:
%Temp%\[RANDOM CHARACTERS].exe
C:\Documents and Settings\<Current User>
C:\Users\<Current User>\AppData\
Delete infected registry values:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableTaskMgr” = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\random
Automatic Removal Tool (Recommended)
SpyHunter is a powerful, real-time anti-spyware application that designed to assist the average computer user in protecting their PC from malicious threats like worms, Trojans, rootkits, rogues, dialers, spyware, etc. It is important to notice that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Video Guide for Your Reference
Notes: If you haven’t sufficient PC expertise and don’t want to make things worse, to remove the Department of Justice Virus infection safely and permanently, click here to download the most popular antivirus program SpyHunter to help you. to clean up the infection in a few minutes without repeating. Hurry up to drag it away from your computer forever!
How to Completely Remove Win32/Alueron.gq (Virus Removal)
Win32/Alueron.gq is a horrible Trojan horse that mainly infects computer users via spam email messages that contain links to when you download it. Once the link is clicked, computers will be infected and start acting weird. Also, computer users can be infected when browsing webpage with hidden malicious codes. In addition, free installation or software downloads that are bundled with this virus as well. When it penetrates into your PC successfully, it begins to modify system settings furtively, which allows it to run automatically every time the Windows is loaded. It’s noticeable that the infected PC will be running in a poorer condition, sometimes getting crashed or Blue Screen. Due to this virus’s infestation, your legit programs, such as Microsoft Word or Web browser, may be shut down frequently and violently. The longer it stays in your PC, the more threats it will bring in. What you have to pay careful attention to is that it creates shortcuts for cyber hackers to keep track of your confidential information for dangerous goals. To protect your computer and privacy, you shall take right action to get rid of it ASAP.
2. It has bad reputation & impact online
3. It spreads to removable drives and other PCs quickly
4. It may bring along all kinds of spyware program
2) The associated files to be removed in folders on Local Disk (note: new files are still created each month so far):
%AllUsersProfile%
%AllUsersProfile%\Application Data\~r
%AllUsersProfile%\Application Data\~dll
3) Open your Registry Editor and then find out the registry entries of Win32/Alueron.gq virus to remove them (note: new registry entries are still made every month so far):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “ ”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” = ’1′
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = ’0′
Important notes: The above mentioned manual removal process is really risky and cumbersome which should be handled with adequate expertise skills. So, this removal job is only suggested for those advanced PC users, because any mistake of removing critical files and registry entries will lead to your computer crash terribly. To get your PC problem resolved successfully within only a short period of time, you’d better click here to download the most popular antivirus program SpyHunter to help you.
Conclusions of Win32/Alueron.gq
1. It invades system without any permission2. It has bad reputation & impact online
3. It spreads to removable drives and other PCs quickly
4. It may bring along all kinds of spyware program
Why I cannot remove Win32/Alueron.gq with antivirus programs?
Not all computer malware could be completely removed by anti-malware programs. Win32/Alueron.gq is one of such stubborn viruses. By using manual method, Win32/Alueron.gq could be stopped and cleaned from toxic computer. To ensure the complete deletion, it’s to stop virus processes, find out and get rid of related files and registry entries. Please follow the step-by-step removal approach below to start.Best way to remove Win32/Alueron.gq manually
1) Boot your computer into safe mode with networking by restarting your computer and keeping pressing F8 key until Windows Advanced Options menu shows up, then using arrow key to select “Safe Mode with Networking” from the list and press ENTER to get into that mode.2) The associated files to be removed in folders on Local Disk (note: new files are still created each month so far):
%AllUsersProfile%
%AllUsersProfile%\Application Data\~r
%AllUsersProfile%\Application Data\~dll
3) Open your Registry Editor and then find out the registry entries of Win32/Alueron.gq virus to remove them (note: new registry entries are still made every month so far):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “ ”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” = ’1′
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = ’0′
Automatic Removal Tool (Recommended)
SpyHunter is a powerful, real-time anti-spyware application that designed to assist the average computer user in protecting their PC from malicious threats like worms, Trojans, rootkits, rogues, dialers, spyware, etc. It is important to notice that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Important notes: The above mentioned manual removal process is really risky and cumbersome which should be handled with adequate expertise skills. So, this removal job is only suggested for those advanced PC users, because any mistake of removing critical files and registry entries will lead to your computer crash terribly. To get your PC problem resolved successfully within only a short period of time, you’d better click here to download the most popular antivirus program SpyHunter to help you.
Tuesday, June 25, 2013
Remove "You Shall Not Pass" Virus Step by Step
"You Shall Not Pass" virus is a stubborn web browser virus that you may have encountered while browsing online through major search engines like Internet Explorer, Mozilla Firefox, Google Chrome and Opera. The possibilities to be infected with this virus may include hacked websites, spam email attachments and sponsored links. Another method is that when you download some freeware from unknown resource without carefulness. Anyway, you should keep vigilant during these similar activities to stay away from this virus. When the You Shall Not Pass infection penetrates into your PC, it begins to perform its annoying campaign. It’s designed by cyber criminals to modify your DNS settings, browser settings, Windows Host files and other important system settings. Thus, every time you visit Google, Yahoo, Bing or any other social sites, You Shall Not Pass virus image will come up that prevents you from viewing your desired content. In addition, it ‘s quite capable of installing additional threats such as fake AV programs, and Trojan onto the contaminated machine, which will further damage the affected system and increase the threat risk. With a machine targeted, it’s no surprised to suffer from system freezing issues, random shutdown slow PC performance and so on. Worse still, it can open a backdoor to facilitate cyber criminals to remotely access the infected PC without your permission. In this situation, your personal information (bank details or all kinds of username or password) will be endangered severely. Without any doubt, you have to get rid of “You Shall Not Pass” virus completely and quickly the moment you detect it on your computer.
Saturday, June 22, 2013
Simply Remove Trojan DOS/Alureon.AB Manually and Quickly
Trojan DOS/Alureon.AB is recognized as a risky Trojan virus designed by cyber criminals to trigger a series of PC annoyance on the infected machine. It spreads globally through junk email attachments, hacked websites and freeware downloads from unknown resource. By seeking system vulnerabilities, this virus sneaks into your computer without any of your permission of awareness. Once installed, it can maximize the damages onto the PC in multi-facets. First of all, it would be launched itself each time when the PC is logged in. There is no surprise to suffer from annoying system freezing issues and casual redirect problem when encountering with this virus. What’s more, the PC performance will be greatly degenerated as the virus is able to eat out a large amount of system resource. With a machine victimized, more and more viruses will be implanted into the PC, making it more hazardous. Summing up, you shall remove Trojan DOS/Alureon.AB as quickly as possible upon detection.
Friday, June 21, 2013
Learn to Remove Trojan Horse BHO.WPO Thoroughly: Virus Manual Removal
 Malignant as Trojan horse BHO.WPO Virus is, it belongs to a hazardous Trojan horse programmed by cybercriminals to endanger target computers seriously in multi-facets. Normally this Trojan proliferates via hacked web sites, sponsored links, insecure shareware or downloads, and so forth. By exploiting system vulnerabilities, it penetrates into users’ computers without any notice by bypassing antivirus software such as AVG and Windows firewall. Don’t simply deem it coming alone. This virus can make the system fragile and facilitate more dangerous threats there which can be malware, spyware, adware, etc. Upon successful installation, it would be amend the system files and registry entries to enable that it would run itself every time the PC launches. It’s noticeable that this bug terribly degrades the PC performance via occupying a large amount of system resource and even triggers system freezing or occasional shutdown issues unexpectedly. Some of your legit programs may even be blocked because of its existence. Another thing that’s worth pointing out here is that cyber hackers design such a Trojan to scam money from reckless PC victims by conducting a serial of harmful campaign. In a word, considering the safety of your system, Trojan horse BHO.WPO must be fixed as quickly as you detect it on your PC.
Malignant as Trojan horse BHO.WPO Virus is, it belongs to a hazardous Trojan horse programmed by cybercriminals to endanger target computers seriously in multi-facets. Normally this Trojan proliferates via hacked web sites, sponsored links, insecure shareware or downloads, and so forth. By exploiting system vulnerabilities, it penetrates into users’ computers without any notice by bypassing antivirus software such as AVG and Windows firewall. Don’t simply deem it coming alone. This virus can make the system fragile and facilitate more dangerous threats there which can be malware, spyware, adware, etc. Upon successful installation, it would be amend the system files and registry entries to enable that it would run itself every time the PC launches. It’s noticeable that this bug terribly degrades the PC performance via occupying a large amount of system resource and even triggers system freezing or occasional shutdown issues unexpectedly. Some of your legit programs may even be blocked because of its existence. Another thing that’s worth pointing out here is that cyber hackers design such a Trojan to scam money from reckless PC victims by conducting a serial of harmful campaign. In a word, considering the safety of your system, Trojan horse BHO.WPO must be fixed as quickly as you detect it on your PC. It’s really horrible to be with Trojan Horse BHO.WPO
1. It invades system without any permission2. It has bad reputation & impact online
3. It spreads to removable drives and other PCs quickly
4. It may bring along all kinds of spyware program
Cannot get rid of Trojan Horse BHO.WPO by security tools?
Your computer is infected by Trojan Horse BHO.WPO but after antivirus AVG cleaned all it indicated, it is coming back after reboot in windows XP, windows vista or windows 7/8? And you have tried many virus removal tools but failed. What scanner does this refer? How do you remove Trojan Horse BHO.WPO without coming back from time to time? Safe and effective manual removal guide (original location) is below.Effective Manual Removal Method
A: Show all hidden files1. Close all programs so that you are at your desktop.
2. Click on the Start button. This is the small round button with the Windows flag in the lower left corner.
3. Click on the Control Panel menu option.
4. When the control panel opens click on the Appearance and Personalization link.
5. Under the Folder Options category, click on Show Hidden Files or Folders.
6. Under the Hidden files and folders section select the radio button labeled Show hidden files, folders, or drives.
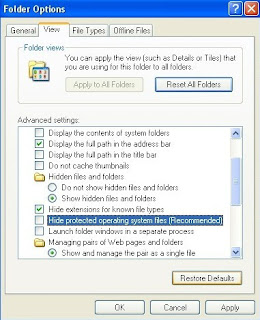
7. Remove the checkmark from the checkbox labeled Hide extensions for known file types.
8. Remove the checkmark from the checkbox labeled Hide protected operating system files (Recommended).
9. Press the Apply button and then the OK button.
B: Manually remove this trojan
1) Restart your PC and before windows interface loads, tap “F8” constantly. Choose “Safe Mode with Networking” option, and then press Enter key.
2) Find and stop Trojan Horse BHO.WPO associated processes:
%APPDATA%\[RANDOM CHARACTERS].js
%APPDATA%\[RANDOM CHARACTERS].pad
%USERPROFILE%\Start Menu\Programs\StartUp\runctf.lnk
4) Detect and remove Trojan Horse BHO.WPO related registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” = ’0′
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = ’1′
Automatic Removal Tool (Recommended)
SpyHunter is a powerful, real-time anti-spyware application that designed to assist the average computer user in protecting their PC from malicious threats like worms, Trojans, rootkits, rogues, dialers, spyware, etc. It is important to notice that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Important notes: Want to safely and completely remove this perky mutating Trojan Horse BHO.WPO virus infection but you cannot figure out a way since various security tools failed to remove it? click here to download the most popular antivirus program SpyHunter to help you.
Uninstall Tango Toolbar - How to Remove Tango
Tango Toolbar is a malicious program that you surely don’t want to keep on your computer. You may get this toolbar unknowingly when you download and install some free application without carefulness. Once it gets inside your machine, you may try to uninstall it from Control Panel add/remove program list but unfortunately, when you open the browser, the thing is still stubbornly on the top of the search engine. From the appearance, it has nothing different from a legitimate toolbar such as Google Toolbar. However, the most obvious difference between them is that Tango is added onto your browser (IE, Firefox or Google Chrome) surreptitiously, which is sponsored by cyber hackers to annoy you with numerous pop-up advertisements. What’s more, it has the ability to modify your default search engine’s settings and keep redirecting you to unwanted web pages. Endless pop ups will make you nearly go nut. The pain of getting such hijack application is far more than those above. With a machine victimized, it will easily facilitate other sorts of infections like Trojan, fake AV program to install onto the system, which would ruin the compromised PC further and help attackers pilfer important data from the victim. You should remove it as soon as possible!
How to Completely Remove Clkmon.com (Virus Uninstall Guide)
Clkmon.com Pops up is classified as nasty web browser hijacker virus that has attacked the increasing number of computer users in the recent periods. You may get infected with the virus unknowingly especially when you download and install something free from insecure resource. As malicious Clkmon.com is, it can take over the browser totally, which could be Internet Explorer, Firefox Mozilla, and Google Chrome. Once inside, it locks the homepage as its domain and modifies the default settings of search engine without direct permission of the user. Even though the user tries to change browser settings and reset the default homepage, only to find all attempts turn to failure. It’s not a piece of cake to figure out this stuff. If your PC is unfortunately infected, you may be forcibly redirected to some sponsored links and websites instead of your actual needs. It is believed that if you carelessly click on one of them, you will go nut to confront lots of troubles from then on. Clkmon.com is actually a privacy-invading advertising domain promoting unwanted adware and malicious products with charming content which aim to induce unsuspected users into jumping its trap. Without any doubts, you should uninstall Clkmon.com as soon as possible when you notice its activities on your machine.
Tips for Removing Lnksr.com Manually and Completely
 Lnksr.com is an infamous browser redirect which can trigger a serial of browser issues that impede your normal web browsing activities. Normally you may get infected with this virus when you visit insalubrious websites, receive spam email attachments, or download some trustless application. Malicious as Lnksr.com is, it affects the main search engines, such as Internet Explorer, Google Chrome and Mozilla Firefox.
Lnksr.com is an infamous browser redirect which can trigger a serial of browser issues that impede your normal web browsing activities. Normally you may get infected with this virus when you visit insalubrious websites, receive spam email attachments, or download some trustless application. Malicious as Lnksr.com is, it affects the main search engines, such as Internet Explorer, Google Chrome and Mozilla Firefox.
Once installed, Lnksr.com will take control of the whole browser by modifying the default browser settings, DNS settings and HOST files. Being a victim of this virus, you may be always redirected to Lnksr.com and its relevant domain promoting unreliable advertisements from which the developer of Lnksr.com can generate revenue or websites containing dangerous Trojans and malware. Furthermore, you may discover your computer runs extremely slow and sometime it gets crashed and freezing issues. Worse still, other kinds of malware or spyware can be implanted onto your PC, which facilitates cyber hackers to monitor your browsing content or online activities. That’s very dangerous, isn’t it? So far there is no security tool that can handle Lnksr.com redirect for it uses rootkit technology to conceal the existence deep in the system.
Step 2: Remove registry entries that lnksr.com has created to your system registry editor:
NOTE: The instruction above is for advanced computer users, since lnksr.com is very tricky, it’s hard to handle it without relative expert skills. You want to remove it ASAP? Please click here to download SpyHunter to automatically fix the virus for you.
lnksr.com is extremely dangerous
* It is a parasitic browser hijacker
* It may show numerous annoying advertisements
* It is installed without your consent
* It will replace (hijack) your browser homepage
* It may spread lots of spyware and adware parasites
* It violates your privacy and compromises your security
* It may show numerous annoying advertisements
* It is installed without your consent
* It will replace (hijack) your browser homepage
* It may spread lots of spyware and adware parasites
* It violates your privacy and compromises your security
Best way to get rid of lnksr.com malware completely
Step 1: Delete files that lnksr.com has added to your system folders and files:
%AllUsersProfile%\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
Step 2: Remove registry entries that lnksr.com has created to your system registry editor:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
Automatic Removal Tool (Recommended)
SpyHunter is a powerful, real-time anti-spyware application that designed to assist the average computer user in protecting their PC from malicious threats like worms, Trojans, rootkits, rogues, dialers, spyware, etc. It is important to notice that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

NOTE: The instruction above is for advanced computer users, since lnksr.com is very tricky, it’s hard to handle it without relative expert skills. You want to remove it ASAP? Please click here to download SpyHunter to automatically fix the virus for you.
Tuesday, June 18, 2013
Easily Get Rid of White Trader (Removal Tips)
White Trader is a harmful adware program that penetrates into random computers unknowingly beyond users’ any permission. This program mainly interrupts victims’ browsing activities by showing numerous annoying advertisements and charming products. Apparently, there are various coupon codes and online promotions implanted onto these ads or sponsored links that are promoted by White Trader. It doesn’t enhance your browser experience, but causes browsing traffic and troublesome PC problems, which makes users freaked out. Maybe White Trader is not a virus itself, but it indeed poses a high risk to an infected system as it keeps redirecting the victim to some hacked websites without any alarm.
Monday, June 17, 2013
Remove Inksdata.com Redirect With Manual Steps
Inksdata.com is a malicious web browser hijacker virus that bothers thousands of PC users worldwide no matter what operation system is installed, which could be Windows XP, vista, Windows 7 and Windows 8. You may get infected occasionally during some illegal online activities, such as downloading something free from insecure resource, opening hacked web pages or legit domain that’s compromised, receiving spam email attachments, and so on. Once it’s downloaded, it will cause many damages to your browser, such as changing your internet browser settings without consent, including the home page, default search engine, and browser shortcuts. Normally it hijacks browsers like IE, Firefox, Google Chrome by constantly redirecting users into its domain where more infections can be facilitated to install onto your PC. With a machine victimized, this virus is able to keep track of your web browsing habits, record addresses of visited sites and send collected data to a remote server without any attention. In conclusion, you have to uninstall Inksdata.com and its accompanied threats quickly the moment you detect it on your PC.
2. Inksdata.com reputation & rating online is terrible
3. It may hijack, redirect and modify your web browser
4. This virus may install other sorts of spyware/adware/malware
5. This virus violates your privacy and compromises your security
%AppData%Local[random].exe
C:\Documents and Settings\LocalService\Local Settings\Temporary Internet Files\*.exe
The registry entries of Inksdata.com that need to be removed are listed as follows: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\random letters
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Important notes: manual removal refers to key parts of computer system. Any error step may lead to system crash. Wanna fix the issue automatically and completely? Please click here to download the most popular antivirus program SpyHunter to help you.
Hazards of Inksdata.com
1. It attacks system without any permission2. Inksdata.com reputation & rating online is terrible
3. It may hijack, redirect and modify your web browser
4. This virus may install other sorts of spyware/adware/malware
5. This virus violates your privacy and compromises your security
Manual removal guide for Inksdata.com
The associated files of Inksdata.com to be deleted are listed below:%AppData%Local[random].exe
C:\Documents and Settings\LocalService\Local Settings\Temporary Internet Files\*.exe
The registry entries of Inksdata.com that need to be removed are listed as follows: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\random letters
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Automatic Removal Tool (Recommended)
SpyHunter is a powerful, real-time anti-spyware application that designed to assist the average computer user in protecting their PC from malicious threats like worms, Trojans, rootkits, rogues, dialers, spyware, etc. It is important to notice that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Important notes: manual removal refers to key parts of computer system. Any error step may lead to system crash. Wanna fix the issue automatically and completely? Please click here to download the most popular antivirus program SpyHunter to help you.
Sunday, June 16, 2013
Remove W32/Patched.UB From Services.exe (Virus Removal)
W32/Patched.UB is a risky Trojan threat which can be implanted into hacked websites, freeware application and junk email messages. Malicious as this infection is, it’s able to damage computer users that range from individual, educational institutions, up to known organizations. Users may discover the virus when running Avira antivirus software. After the scan, it’s located in C:\Windows\System32\services.exe but can never be deleted by any antivirus. This is because advanced rootkit technology is utilized to conceal the existence deep and bypass antivirus’ detection. Once getting inside a machine, w32/Patched.UB would be configured to run automatically whenever you turn on the machine. Since it creates lots of unnecessary infected files and registry values, the compromised PC will be running in extremely poor condition. Sometime, it even gets redirected to unwanted web pages during browsing online. The longer time you stay with W32/Patched.UB, the more hazards it will bring in. What’s the terrifying aspect of this virus is that it creates shortcuts for cybercriminals to gain access your machine and control over the infected PC. As a consequence, your precious data, such as bank details, credit card information will be opened to the public. To sum up, W32/Patched.UB must be fixed immediately when it’s detected on your computer.
Saturday, June 15, 2013
Trojan horse generic29.ahhs Removal Guide
Trojan horse Generic 29.AHHS virus is a risky Trojan that can easily get installed onto random computers when users gain access to hacked web pages or harmful downloads from unknown recourse. Once activated, it would run itself automatically together with each system’s startup by messing up system registries and files without any permission of the user. Please don’t simply deem this virus comes alone, but it’s accompanied with other dangerous threats such as fake AV programs, adware parasites, etc. Trojan horse Generic29.AHHS is good at seeking system vulnerabilities for cyber criminals to visit the victimized computer remotely and pilfer unwary users’ sensitive personal information as much as possible for corrupted goals. What’s more, such a Trojan can also degenerate system performance, cause high CPU usage and disable function of executable programs miserably. That’s why your security applications and firewall protection fail to catch the Trojan horse entirely. To ensure a complete and efficient cleanup, you need to remove the Trojan horse Generic29.AHHS virus manually from the contaminated machine. Please conduct the continuous reading of this article.
Thursday, June 13, 2013
Remove "this file contained a virus and was deleted" from your computer
"This Program (or this file) contained a virus and was deleted” is a fake alert showing on Internet Explorer 8, 9 or 10 when computer users try to download a file or program via the internet. If you see this message pop-up, then your PC is infected with a ZeroAccess rootkit. Both of them have intimate relationship that can function in all the Windows operation system, which may could be Window 7, Windows 8, Windows XP, or vista. Once victimized, you’ll be blocked miserably from downloading any file or program, leaving the warning notification “this file contained a virus and was deleted” again and again. Till now, this virus has only targeted Internet Explorer while other people who’re using Firefox or Chrome will not receive this alert. Though this virus appeared a long time ago, it’s still made many users upset. Some of them may complain about the poor PC performance and even random system freezing issues once the virus’s already on board. Then they’re very likely to try antivirus as the first choice to get rid of this pest, however, after scanning, the antivirus found no threat but the annoying message comes up when downloading something from the internet. Keep in mind that “this proglram contained a virus and was deleted” virus is stubborn enough to bypass various security tools’ detection. Worse still, it’s triggered by a Trojan which can contact a remote server and install other malware including fake AV programs onto the compromised machine. You have to get rid of “file contained a virus and was deleted” immediately once it’s discovered in the PC. For a safe and complete guide, please follow the specific post as explained below. If you’re not a computer literate, you’d better consult online tech experts to avoid irreparable damages.
1. Launch the Task Manager by pressing keys Ctrl+Alt+Del or Ctrl+Shift+Esc at the same time, search for "this file contained a virus and was deleted" processes and right-click to end them.
2. Open Control Panel in Start menu and search for Folder Options. When you’re in Folder Options window, please click on its View tab, check Show hidden files and folders and uncheck Hide protected operating system files (Recommended) and then press OK.
3. Tap Windows+R keys together to pop up the Run box, type in regedit and hit OK to open Registry Editor; then find out the following "file contained a virus and was deleted" registry entries and delete:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\[random]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run\[random]
4. Get rid of the listed files created by "file contained a virus and was deleted" :
%System%\[random].exe
%Temp%\[random].bat
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
NOTE: If you haven’t sufficient expertise in handling virus program files, processes, dll files and registry entries, you will take the risk of messing up your computer and making it crash down finally. If you need automatic removal help, click here to download the most popular antivirus program SpyHunter to help you.
How to delete this "file contained a virus and was deleted" virus from your PC?
Before performing the manual removal of "this file contained a virus and was deleted", reboot your computer and before Windows interface loads, press F8 key constantly. Choose "Safe Mode with Networking” option, and then press Enter key. System will load files and then get to the desktop in needed option.1. Launch the Task Manager by pressing keys Ctrl+Alt+Del or Ctrl+Shift+Esc at the same time, search for "this file contained a virus and was deleted" processes and right-click to end them.
2. Open Control Panel in Start menu and search for Folder Options. When you’re in Folder Options window, please click on its View tab, check Show hidden files and folders and uncheck Hide protected operating system files (Recommended) and then press OK.
3. Tap Windows+R keys together to pop up the Run box, type in regedit and hit OK to open Registry Editor; then find out the following "file contained a virus and was deleted" registry entries and delete:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\[random]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run\[random]
4. Get rid of the listed files created by "file contained a virus and was deleted" :
%System%\[random].exe
%Temp%\[random].bat
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
Automatic Removal Tool (Recommended)
SpyHunter is a powerful, real-time anti-spyware application that designed to assist the average computer user in protecting their PC from malicious threats like worms, Trojans, rootkits, rogues, dialers, spyware, etc. It is important to notice that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Video tutorials for your reference
NOTE: If you haven’t sufficient expertise in handling virus program files, processes, dll files and registry entries, you will take the risk of messing up your computer and making it crash down finally. If you need automatic removal help, click here to download the most popular antivirus program SpyHunter to help you.
Trojan Horse Generic29.AJGE Removal: How to Remove Trojan Generic29.AJGE
 Trojan horse Generic29.AJGE is a sneaky cyber threat which comes from the Trojan category. Malicious as Trojan Generic29.AJGE is, it’s created by cyber criminals to take over the whole infected computer and trigger lots of destruction to the naïve victim. Generally speaking, this virus can easily break onto a machine when the user accidentally download and install free software from unknown recourse, open pornographic web pages, or click on sponsored links, receive spam emails from hackers. It’s such a horrible threat that can attack PC system with Windows operation system worldwide. Once installed onto your machine, it’s able to consume high PC recourse, thus no doubt that you’ll suffer from a sluggish machine with causal shutdown or freezing issues. Moreover, under the help of this Trojan, remote hackers can easily gain access your PC in the background and collect your confidential information including bank account or credit card details, social contact information and so on. In this situation, your personal data will be opened to the pubic seriously. If there is no immediate cleanup, it can facilitate more infections to your system, increasing the difficulty to the removal. Being a victim of this virus, you’re not surprised to witness the virus traces every time you power on the machine.
Trojan horse Generic29.AJGE is a sneaky cyber threat which comes from the Trojan category. Malicious as Trojan Generic29.AJGE is, it’s created by cyber criminals to take over the whole infected computer and trigger lots of destruction to the naïve victim. Generally speaking, this virus can easily break onto a machine when the user accidentally download and install free software from unknown recourse, open pornographic web pages, or click on sponsored links, receive spam emails from hackers. It’s such a horrible threat that can attack PC system with Windows operation system worldwide. Once installed onto your machine, it’s able to consume high PC recourse, thus no doubt that you’ll suffer from a sluggish machine with causal shutdown or freezing issues. Moreover, under the help of this Trojan, remote hackers can easily gain access your PC in the background and collect your confidential information including bank account or credit card details, social contact information and so on. In this situation, your personal data will be opened to the pubic seriously. If there is no immediate cleanup, it can facilitate more infections to your system, increasing the difficulty to the removal. Being a victim of this virus, you’re not surprised to witness the virus traces every time you power on the machine. Sunday, June 9, 2013
Trojan Horse Generic32.CEMU Virus Removal
Trojan Horse Generic32.CEMU is a highly dangerous Trojan threat that can mess up target computers a lot in multi-facets. As horrible Trojan Horse Generic32.CEMU is, it’s mainly used by cyber hackers to open a backdoor on the infected PC so that it can drop additional adware or spyware into the contaminated system. Once installed onto your machine, this virus will load lots of evil processes to consume high amount of system resource and reset the default settings to allow its re-appearance constantly. Besides, it will change your desktop background and display various fake security messages to scary users into thinking that their PCs are in high danger. At times, it redirects users into unwanted web pages while surfing the internet as it modifies browser setting without direct permission. What’s worse, this malicious item violates your privacy and compromises your security by keeping track of your browsing history and computer data.
# It can compromise your system and may introduce additional infections like rogue software.
# You may be redirected to some unsafe websites and advertisements which are not trusted.
# The Trojan often takes up high resources and strikingly slow down your computer speed.
# The virus can help the cyber criminals to track your computer and steal your personal information.
To perform this procedure, please restart your computer and keep pressing F8 key until Windows Advanced Options menu shows up, then using arrow key to select “Safe Mode with Networking” from the list and press ENTER to get into that mode.
2) Press Ctrl+Alt+Del keys together to pull up Window Task Manager and end suspicious processes:
3) Check the following directories and remove all these associated files:
%APPDATA%\[RANDOM CHARACTERS].js
%APPDATA%\[RANDOM CHARACTERS].pad
%USERPROFILE%\Start Menu\Programs\StartUp\runctf.lnk
4) Open Registry Editor by navigating to Start Menu, type in Regedit, and then click OK. When you have been in Registry Editor, please remove the following related registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” = ’0′
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = ’1′
5) After you finish the above steps, please reboot your computer and get in normal mode to check the effectiveness.
How to avoid being entangled by virus like Trojan Horse Generic32.CEMU?1. Never click on a link or attachment in an email that you are not positive is from a trusted source;
2. Beware of internet pop-ups;
3. Set up your Windows Update to automatically download patches and upgrades;
4. Be wary of files with a double extension such as .txt.vb or .jpg.exe.
5. Install real-time anti-spyware protection and Keep anti-malware applications current.
6. Don’t get access to illegal online contents such as gambling or porn.
Notes: If you haven’t sufficient expertise in handling virus program files, processes, dll files and registry entries, you will take the risk of messing up your computer and making it crash down finally. Click here to download SpyHunter to automatically fix the virus for you.
Dangers of Trojan Horse Generic32.CEMU threat
# It comes without any consent and disguises itself in root of the system once installed.# It can compromise your system and may introduce additional infections like rogue software.
# You may be redirected to some unsafe websites and advertisements which are not trusted.
# The Trojan often takes up high resources and strikingly slow down your computer speed.
# The virus can help the cyber criminals to track your computer and steal your personal information.
Basic steps to delete Trojan Horse Generic32.CEMU manually
1) Boot your computer into Safe Mode with Networking.To perform this procedure, please restart your computer and keep pressing F8 key until Windows Advanced Options menu shows up, then using arrow key to select “Safe Mode with Networking” from the list and press ENTER to get into that mode.
2) Press Ctrl+Alt+Del keys together to pull up Window Task Manager and end suspicious processes:
3) Check the following directories and remove all these associated files:
%APPDATA%\[RANDOM CHARACTERS].js
%APPDATA%\[RANDOM CHARACTERS].pad
%USERPROFILE%\Start Menu\Programs\StartUp\runctf.lnk
4) Open Registry Editor by navigating to Start Menu, type in Regedit, and then click OK. When you have been in Registry Editor, please remove the following related registry entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” = ’0′
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = ’1′
5) After you finish the above steps, please reboot your computer and get in normal mode to check the effectiveness.
Automatic Removal Tool (Recommended)
SpyHunter is a powerful, real-time anti-spyware application that designed to assist the average computer user in protecting their PC from malicious threats like worms, Trojans, rootkits, rogues, dialers, spyware, etc. It is important to notice that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

How to avoid being entangled by virus like Trojan Horse Generic32.CEMU?1. Never click on a link or attachment in an email that you are not positive is from a trusted source;
2. Beware of internet pop-ups;
3. Set up your Windows Update to automatically download patches and upgrades;
4. Be wary of files with a double extension such as .txt.vb or .jpg.exe.
5. Install real-time anti-spyware protection and Keep anti-malware applications current.
6. Don’t get access to illegal online contents such as gambling or porn.
Notes: If you haven’t sufficient expertise in handling virus program files, processes, dll files and registry entries, you will take the risk of messing up your computer and making it crash down finally. Click here to download SpyHunter to automatically fix the virus for you.
Tuesday, June 4, 2013
Trojan PSW.Generic11.PWD Virus Removal
Recently, Trojan PSW.Generic11.PWD has come up and soon become a terrible Trojan virus that installs onto target computer furtively without users’ permission. It’s good at making use of security blunders of Windows including Windows Xp, vista or Win 7 and Win 8. It’s very likely to be infected with this virus when people visit malicious websites, download unknown freeware and open spam email attachments. To be general, it can be reported and quarantined by some popular antivirus, but it’s always able to evade the deletion of any security software with rootkit technology. Hence, it’s no surprise to keep receiving the notifications of the virus after each reboot though it seemed to be removed. Keep in mind that there is no perfect antivirus that can solve everything in the world due to the changeable characteristics of the virus.
Cloudfront.net Removal: How to Remove Redirect Virus
Cloudfront.net is a notorious browser hijacker that’s able to redirect users’ internet activities to its domain or unwanted pages without permission. It’s such a tricky and stubborn virus that it varies its location in a compromised machine all the time with advanced rootkit technology. Your installed antivirus software may detect the existence of this virus but it’s always unable to eradicate it indeed. Cloudfront.net gets into your machine surreptitiously together with some free software, unknown email attachments and pornographic content images or videos. Being a hazardous redirect infection, it has the ability to take over browsers, i.e. Firefox, Internet Explorer and Google Chrome. If you’re encountered with this bug, your default homepage will be locked at Cloudfront.net and it seems impossible for you to change it back to your favorite. Each time you search for something on Google, Bing or any other major search engine, the results will be redirected to some unwanted suspicious websites full of dubious advertisements from which the hackers can earn money by utilizing pay-per-click technique. In worse case, your private information will be opened to the public so that the attackers can pilfer and transfer it to an unknown remote server for illicit use. To sum up, Cloudfront.net should be fixed immediately before further damages from it.
Monday, June 3, 2013
How to Remove en.v9.com (http://en.v9.com) Hijacker Virus: Removal Support
 v9 redirect (aka Search.v9.com or en.v9.com) is a risky web browser hijacker infection that must be fixed immediately the moment you detect it on the machine. Generally speaking, this stubborn virus may propagate in quick speed via malicious websites, unknown email attachments, free software downloads, etc. Though your computer is under the protection of antivirus programs, it can exploit rootkit technology to breezily shun them and stubbornly reside in the PC. If you’re unfortunately infected with this virus, do not simply regard it as a real search because it would trigger many harmful PC issues in multi-facets. Upon installed, this bug will replace your homepage without your permission, and you will discover that it is very hard to change it back. It forcedly takes control of your search engine (such as IE, Firefox or Google) and even when you open a new tap, this virus will come up again. How pesky it is! The longer time it stays in the PC, the more threats it will bring, which would endanger the compromised system to a further extent. Entangled by v9 domain, you may have no other choice but use it to search, however, if you try to type something in the http://en.v9.com search box, the results will be pointed to some harmful web pages filled with advertisement pop-ups which are generated by those virus makers or its sponsors. To completely and safely uninstall v9 virus, manual removal is highly appreciated since antivirus software doesn’t assist to remove it. Here is a useful post for you.
v9 redirect (aka Search.v9.com or en.v9.com) is a risky web browser hijacker infection that must be fixed immediately the moment you detect it on the machine. Generally speaking, this stubborn virus may propagate in quick speed via malicious websites, unknown email attachments, free software downloads, etc. Though your computer is under the protection of antivirus programs, it can exploit rootkit technology to breezily shun them and stubbornly reside in the PC. If you’re unfortunately infected with this virus, do not simply regard it as a real search because it would trigger many harmful PC issues in multi-facets. Upon installed, this bug will replace your homepage without your permission, and you will discover that it is very hard to change it back. It forcedly takes control of your search engine (such as IE, Firefox or Google) and even when you open a new tap, this virus will come up again. How pesky it is! The longer time it stays in the PC, the more threats it will bring, which would endanger the compromised system to a further extent. Entangled by v9 domain, you may have no other choice but use it to search, however, if you try to type something in the http://en.v9.com search box, the results will be pointed to some harmful web pages filled with advertisement pop-ups which are generated by those virus makers or its sponsors. To completely and safely uninstall v9 virus, manual removal is highly appreciated since antivirus software doesn’t assist to remove it. Here is a useful post for you.Impact of en.v9.com virus
1. It gets into systems without any permission;
2. en.v9.com Center's reputation & rating online is terrible;
3. en.v9.com may affect and modify compromised computers' important system files;
4. en.v9.com may install other sorts of spyware/adware without computer users' knowledge.
2. en.v9.com Center's reputation & rating online is terrible;
3. en.v9.com may affect and modify compromised computers' important system files;
4. en.v9.com may install other sorts of spyware/adware without computer users' knowledge.
Best way to terminate en.v9.com malware completely
Method one: Add / Remove Program
Most of the time, we can use Add / Remove Program to remove the programs we choose, for it is a built-in program which helps Windows users to manage their PC. Also, with the help of it, you are able to add or delete program as you want.
1. Find the “start” button on the lower left corner of your monitor, and then click it.
2. Find and double click the button “Control Panel”.
3. Find “Add / Remove Program” icon in the control panel, and then double click it.
4. When the windows pop up, find en.v9.com icon in the list, and then select it to start uninstalling it from your computer by clicking “Remove”.
5. When it is finished, reboot your computer to take effect.
Method two: General removal
Reboot the PC and keep pressing F8 key on the keyboard upon PC startup but before logging in. Hit the arrow keys to choose "Safe Mode with Networking" option, and then tap Enter key to enter Safe Mode with Networking.
Kill malicious processes:
[random].exe
Delete infected files:
C:\WINDOWS\assembly\KYH_64\Desktop.ini
C:\Windows\assembly\KYH_32\Desktop.ini
C:\WINDOWS\system32\giner.exe
Delete infected registry values:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\run\random
HKEY_CURRENT_USER\Software\Microsoft\Installer\Products\5ATIUYW62OUOMNBX256 “(Default)”=”1?
C:\Windows\assembly\KYH_32\Desktop.ini
C:\WINDOWS\system32\giner.exe
Delete infected registry values:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\run\random
HKEY_CURRENT_USER\Software\Microsoft\Installer\Products\5ATIUYW62OUOMNBX256 “(Default)”=”1?
Automatic Removal Tool (Recommended)
SpyHunter is a powerful, real-time anti-spyware application that designed to assist the average computer user in protecting their PC from malicious threats like worms, Trojans, rootkits, rogues, dialers, spyware, etc. It is important to notice that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

NOTE: manual removal of en.v9.com is known as the most effective way. Anyway, it refers to key parts of computer system, and is recommended only for advanced users. If you have not sufficient expertise on doing that, you may face risk of damaging the computer. In this circumstance, you're advised to click here to download SpyHunter to automatically fix the virus for you.
Tips for Removing ueep (http://search.ueep.com/) Redirect Virus
 ueep.com (http://search.ueep.com/) is presented as a malicious browser hijacker that designed by cyber hackers to interrupt users’ browser activities without their permission. The installation of this redirect is often performed surreptitiously especially when the users are visiting insalubrious websites, downloading insecure applications, or opening spam email attachments. After breaking onto a machine, search.ueep.com is able to take over the current search engine in the PC, which may include Firefox, Internet Explorer and Google Chrome. By exploiting system vulnerabilities, this infection will change some of the Internet settings easily so that it can replace the default homepage and search engine. Even though the user reinstalls the browser, such virus still appears during online browsing, triggering constant redirect issues. In this situation, additional threats will be facilitated to install onto the compromised machine, which increases the difficulty to the removal as well as endangering the machine more severely. What’s worth mentioning here is that the advertisements and sponsors links contained in the virus domain are distrustful. Don’t deem http://search.ueep.com/ as the real search engine as Google, Yahoo, Bing, it’s in fact a browser hijack redirect that aims to rip people off for money. If you have being suffered from this virus, please take immediate actions to remove it completely.
ueep.com (http://search.ueep.com/) is presented as a malicious browser hijacker that designed by cyber hackers to interrupt users’ browser activities without their permission. The installation of this redirect is often performed surreptitiously especially when the users are visiting insalubrious websites, downloading insecure applications, or opening spam email attachments. After breaking onto a machine, search.ueep.com is able to take over the current search engine in the PC, which may include Firefox, Internet Explorer and Google Chrome. By exploiting system vulnerabilities, this infection will change some of the Internet settings easily so that it can replace the default homepage and search engine. Even though the user reinstalls the browser, such virus still appears during online browsing, triggering constant redirect issues. In this situation, additional threats will be facilitated to install onto the compromised machine, which increases the difficulty to the removal as well as endangering the machine more severely. What’s worth mentioning here is that the advertisements and sponsors links contained in the virus domain are distrustful. Don’t deem http://search.ueep.com/ as the real search engine as Google, Yahoo, Bing, it’s in fact a browser hijack redirect that aims to rip people off for money. If you have being suffered from this virus, please take immediate actions to remove it completely. Search.ueep.com is very dangerous
* It is a parasitic browser hijacker
* It may show numerous annoying advertisements
* It is installed without your consent
* It will replace (hijack) your browser homepage
* It may spread lots of spyware and adware parasites
* It violates your privacy and compromises your security
* It may show numerous annoying advertisements
* It is installed without your consent
* It will replace (hijack) your browser homepage
* It may spread lots of spyware and adware parasites
* It violates your privacy and compromises your security
Follow the manual tutorials to delete ueep redirect
Manual removal is a huge process and a risky method to cause irreversible manmade damage to your computer. If you are not professional, please immediately contact your friends who are very good at computer and have much manual virus removal experience for help! What if I don’t have such kind of friend? - See the recommended method below.1. To stop all ueep processes, press CTRL+ALT+DELETE to open the Windows Task Manager.
2. Click on the "Processes" tab, search for ueep, then right-click it and select "End Process" key.
3. Click "Start" button and selecting "Run." Type "regedit" into the box and click "OK."
4. Once the Registry Editor is open, search for the registry key "HKEY_LOCAL_MACHINE\Software\ ueep." Right-click this registry key and select "Delete."
5. Navigate to directory %PROGRAM_FILES%\ ueep\ and delete the infected files manually.
C:\WINDOWS\assembly\KYH_64\Desktop.ini
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\run\random
Automatic Removal Tool (Recommended)
SpyHunter is a powerful, real-time anti-spyware application that designed to assist the average computer user in protecting their PC from malicious threats like worms, Trojans, rootkits, rogues, dialers, spyware, etc. It is important to notice that SpyHunter removal tool works well and should run alongside existing security programs without any conflicts.
Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Step 1. Click the Download icon below to install SpyHunter on your PC.

Step 2. After the installation, run SpyHunter and click “Malware Scan” button to have a full or quick scan on your computer.

Step 3. Choose Select all>Remove to get rid of all the detected threats on your PC.

Note: If you haven't sufficient expertise in dealing with program files, processes, .dll files and registry entries, you're welcome to click here to download SpyHunter to automatically fix the ueep virus for you.